Cyber Attacks/Data Breaches
Ex-twitter employee gets 42 months for taking $300,000 bribe and sharing confidential information of twitter accounts.

Cyber Attacks/Data Breaches
Founder of BreachForums, a cybercrime website, got 20 years of supervised release without prison time.
Cyber Attacks/Data Breaches
Australia, U.K and U.S. have imposed financial penalties on a Russian Hacker for his role in the 2022 cyberattack on Medibank
Cyber Attacks/Data Breaches
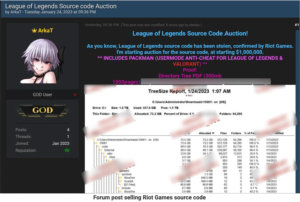
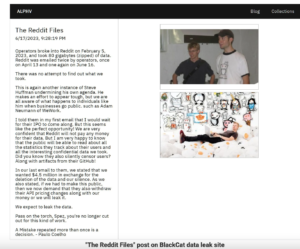
Reddit hackers are threatening to release the stolen data from the February breach.
-

 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years agoSquarePhish: QR Code and Auth Device Code authentication Phishing tool
-

 Vulnerabilities/Malwares3 years ago
Vulnerabilities/Malwares3 years agoHyundai and Kia patch a bug that allowed USB cable car thefts.
-

 Malwares3 years ago
Malwares3 years agoCybercriminals Use the Powerful BatCloak Engine to make malware undetected by AntiVirus
-

 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years agoHackBrowserData: Decrypt passwords/cookies/history/bookmarks from the browser
-

 Windows/Mac/Linux4 years ago
Windows/Mac/Linux4 years agoGoogle caught North Korean Hackers Using Chrome Browser Exploit on Americans
-

 Cyber Attacks/Data Breaches4 years ago
Cyber Attacks/Data Breaches4 years agoHackers from the Russian Federation have continued to launch attacks on Ukrainian organisations with info-stealer malware.
-

 Mobile Hacking3 years ago
Mobile Hacking3 years agoWhatsApp now supports proxy servers to bypass government restrictions.
-

 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years agoRemotely exploiting Android devices using ADB (Android Debug Bridge) and Metasploit-Framework.