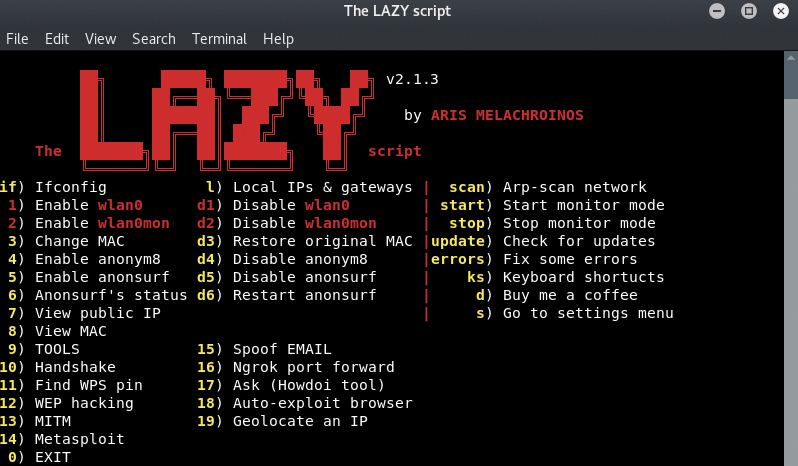
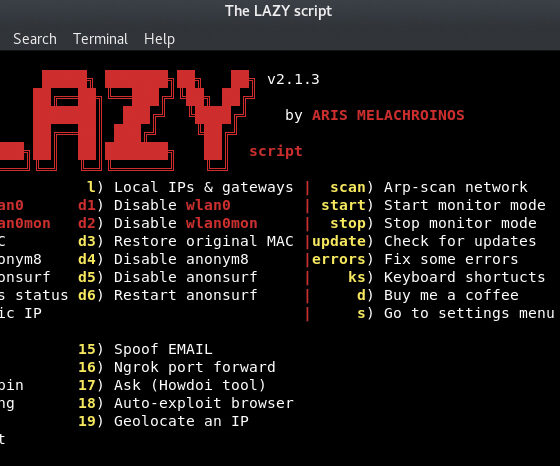
Welcome to the LAZY script v2.1.4 A video Hackersploit made : https://www.youtube.com/watch?v=oBpo5sElrMY A video sstec made: https://www.youtube.com/watch?v=gSO7c2MN7TY For feature-recommendation ,...


Fluxion is the future of MITM WPA attacks Fluxion is a security auditing and social-engineering research tool. It is a remake of linset by vk496 with...


Cloning: git clone https://github.com/4w4k3/BeeLogger.git Running: cd BeeLogger sudo su chmod +x install.sh ./install.sh python bee.py If you have another version of Python: python2.7 bee.py DISCLAIMER: “DISCLAIMED....


PhoneSploit Pro PhoneSploit with Metasploit Integration. An all-in-one hacking tool written in Python to remotely exploit Android devices using ADB (Android Debug Bridge) and Metasploit-Framework. Complete Automation to get a...


Anonymously Hiding Tools Information gathering tools Wordlist Generator Wireless attack tools SQL Injection Tools Phishing attack tools Web Attack tools Post exploitation tools Forensic tools Payload...

Threat actors are switching from paid options like Cobalt Strike and Brute Ratel to a new open-source command and control (C2) framework called Havoc, according to...


Shennina Automating Host Exploitation with AI Abstract Shennina is an automated host exploitation framework. The mission of the project is to fully automate the scanning, vulnerability...


SquarePhish SquarePhish is an advanced phishing tool that uses a technique combining the OAuth Device code authentication flow and QR codes. See PhishInSuits for more details on using...


README.md [Website] [Blog] [Shop] [Documentation] [Demo] [Find Out More] Attack Surface Management Discover hidden assets and vulnerabilities in your environment [Find out more] The ultimate...


K🔑Logger v3.0.0 Description Remote persistent 🔑Logger for Windows and Linux Features Logs keys pressed on keyboard upload reports in anonfile. Works with Linux and Windows. Does not require...