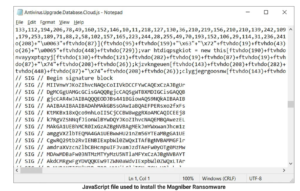
| Tag |
CVE ID |
CVE Title |
Severity |
| .NET Framework |
CVE-2022-41089 |
.NET Framework Remote Code Execution Vulnerability |
Important |
| Azure |
CVE-2022-44699 |
Azure Network Watcher Agent Security Feature Bypass Vulnerability |
Important |
| Client Server Run-time Subsystem (CSRSS) |
CVE-2022-44673 |
Windows Client Server Run-Time Subsystem (CSRSS) Elevation of Privilege Vulnerability |
Important |
| Microsoft Bluetooth Driver |
CVE-2022-44675 |
Windows Bluetooth Driver Elevation of Privilege Vulnerability |
Important |
| Microsoft Bluetooth Driver |
CVE-2022-44674 |
Windows Bluetooth Driver Information Disclosure Vulnerability |
Important |
| Microsoft Dynamics |
CVE-2022-41127 |
Microsoft Dynamics NAV and Microsoft Dynamics 365 Business Central (On Premises) Remote Code Execution Vulnerability |
Critical |
| Microsoft Edge (Chromium-based) |
CVE-2022-4192 |
Chromium: CVE-2022-4192 Use after free in Live Caption |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4193 |
Chromium: CVE-2022-4193 Insufficient policy enforcement in File System API |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4190 |
Chromium: CVE-2022-4190 Insufficient data validation in Directory |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4191 |
Chromium: CVE-2022-4191 Use after free in Sign-In |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4194 |
Chromium: CVE-2022-4194 Use after free in Accessibility |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-41115 |
Microsoft Edge (Chromium-based) Update Elevation of Privilege Vulnerability |
Important |
| Microsoft Edge (Chromium-based) |
CVE-2022-44688 |
Microsoft Edge (Chromium-based) Spoofing Vulnerability |
Moderate |
| Microsoft Edge (Chromium-based) |
CVE-2022-4195 |
Chromium: CVE-2022-4195 Insufficient policy enforcement in Safe Browsing |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-44708 |
Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability |
Important |
| Microsoft Edge (Chromium-based) |
CVE-2022-4181 |
Chromium: CVE-2022-4181 Use after free in Forms |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4180 |
Chromium: CVE-2022-4180 Use after free in Mojo |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4174 |
Chromium: CVE-2022-4174 Type Confusion in V8 |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4182 |
Chromium: CVE-2022-4182 Inappropriate implementation in Fenced Frames |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4179 |
Chromium: CVE-2022-4179 Use after free in Audio |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4178 |
Chromium: CVE-2022-4178 Use after free in Mojo |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4175 |
Chromium: CVE-2022-4175 Use after free in Camera Capture |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4177 |
Chromium: CVE-2022-4177 Use after free in Extensions |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4187 |
Chromium: CVE-2022-4187 Insufficient policy enforcement in DevTools |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4185 |
Chromium: CVE-2022-4185 Inappropriate implementation in Navigation |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4188 |
Chromium: CVE-2022-4188 Insufficient validation of untrusted input in CORS |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4189 |
Chromium: CVE-2022-4189 Insufficient policy enforcement in DevTools |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4186 |
Chromium: CVE-2022-4186 Insufficient validation of untrusted input in Downloads |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4183 |
Chromium: CVE-2022-4183 Insufficient policy enforcement in Popup Blocker |
Unknown |
| Microsoft Edge (Chromium-based) |
CVE-2022-4184 |
Chromium: CVE-2022-4184 Insufficient policy enforcement in Autofill |
Unknown |
| Microsoft Graphics Component |
CVE-2022-26805 |
Microsoft Office Graphics Remote Code Execution Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-26804 |
Microsoft Office Graphics Remote Code Execution Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-47213 |
Microsoft Office Graphics Remote Code Execution Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-44697 |
Windows Graphics Component Elevation of Privilege Vulnerability |
Moderate |
| Microsoft Graphics Component |
CVE-2022-41121 |
Windows Graphics Component Elevation of Privilege Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-44671 |
Windows Graphics Component Elevation of Privilege Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-47212 |
Microsoft Office Graphics Remote Code Execution Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-26806 |
Microsoft Office Graphics Remote Code Execution Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-47211 |
Microsoft Office Graphics Remote Code Execution Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-41074 |
Windows Graphics Component Information Disclosure Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-44679 |
Windows Graphics Component Information Disclosure Vulnerability |
Important |
| Microsoft Graphics Component |
CVE-2022-44680 |
Windows Graphics Component Elevation of Privilege Vulnerability |
Important |
| Microsoft Office |
CVE-2022-44692 |
Microsoft Office Graphics Remote Code Execution Vulnerability |
Important |
| Microsoft Office OneNote |
CVE-2022-44691 |
Microsoft Office OneNote Remote Code Execution Vulnerability |
Important |
| Microsoft Office Outlook |
CVE-2022-24480 |
Outlook for Android Elevation of Privilege Vulnerability |
Important |
| Microsoft Office Outlook |
CVE-2022-44713 |
Microsoft Outlook for Mac Spoofing Vulnerability |
Important |
| Microsoft Office SharePoint |
CVE-2022-44690 |
Microsoft SharePoint Server Remote Code Execution Vulnerability |
Critical |
| Microsoft Office SharePoint |
CVE-2022-44693 |
Microsoft SharePoint Server Remote Code Execution Vulnerability |
Critical |
| Microsoft Office Visio |
CVE-2022-44696 |
Microsoft Office Visio Remote Code Execution Vulnerability |
Important |
| Microsoft Office Visio |
CVE-2022-44695 |
Microsoft Office Visio Remote Code Execution Vulnerability |
Important |
| Microsoft Office Visio |
CVE-2022-44694 |
Microsoft Office Visio Remote Code Execution Vulnerability |
Important |
| Microsoft Windows Codecs Library |
CVE-2022-44668 |
Windows Media Remote Code Execution Vulnerability |
Important |
| Microsoft Windows Codecs Library |
CVE-2022-44667 |
Windows Media Remote Code Execution Vulnerability |
Important |
| Microsoft Windows Codecs Library |
CVE-2022-44687 |
Raw Image Extension Remote Code Execution Vulnerability |
Important |
| Role: Windows Hyper-V |
CVE-2022-41094 |
Windows Hyper-V Elevation of Privilege Vulnerability |
Important |
| Role: Windows Hyper-V |
CVE-2022-44682 |
Windows Hyper-V Denial of Service Vulnerability |
Important |
| SysInternals |
CVE-2022-44704 |
Microsoft Windows Sysmon Elevation of Privilege Vulnerability |
Important |
| Windows Certificates |
ADV220005 |
Guidance on Microsoft Signed Drivers Being Used Maliciously |
None |
| Windows Contacts |
CVE-2022-44666 |
Windows Contacts Remote Code Execution Vulnerability |
Important |
| Windows DirectX |
CVE-2022-44710 |
DirectX Graphics Kernel Elevation of Privilege Vulnerability |
Important |
| Windows Error Reporting |
CVE-2022-44669 |
Windows Error Reporting Elevation of Privilege Vulnerability |
Important |
| Windows Fax Compose Form |
CVE-2022-41077 |
Windows Fax Compose Form Elevation of Privilege Vulnerability |
Important |
| Windows HTTP Print Provider |
CVE-2022-44678 |
Windows Print Spooler Elevation of Privilege Vulnerability |
Important |
| Windows Kernel |
CVE-2022-44707 |
Windows Kernel Denial of Service Vulnerability |
Important |
| Windows Kernel |
CVE-2022-44683 |
Windows Kernel Elevation of Privilege Vulnerability |
Important |
| Windows PowerShell |
CVE-2022-41076 |
PowerShell Remote Code Execution Vulnerability |
Critical |
| Windows Print Spooler Components |
CVE-2022-44681 |
Windows Print Spooler Elevation of Privilege Vulnerability |
Important |
| Windows Projected File System |
CVE-2022-44677 |
Windows Projected File System Elevation of Privilege Vulnerability |
Important |
| Windows Secure Socket Tunneling Protocol (SSTP) |
CVE-2022-44670 |
Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
Critical |
| Windows Secure Socket Tunneling Protocol (SSTP) |
CVE-2022-44676 |
Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
Critical |
| Windows SmartScreen |
CVE-2022-44698 |
Windows SmartScreen Security Feature Bypass Vulnerability |
Moderate |
| Windows Subsystem for Linux |
CVE-2022-44689 |
Windows Subsystem for Linux (WSL2) Kernel Elevation of Privilege Vulnerability |
Important |
| Windows Terminal |
CVE-2022-44702 |
Windows Terminal Remote Code Execution Vulnerability |
Important |


 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years ago
 Vulnerabilities/Malwares3 years ago
Vulnerabilities/Malwares3 years ago
 Malwares3 years ago
Malwares3 years ago
 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years ago
 Windows/Mac/Linux4 years ago
Windows/Mac/Linux4 years ago
 Cyber Attacks/Data Breaches4 years ago
Cyber Attacks/Data Breaches4 years ago
 Mobile Hacking3 years ago
Mobile Hacking3 years ago
 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years ago