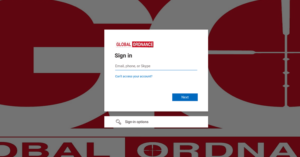
An attack infrastructure that spoofs the Microsoft login page of Global Ordnance, a legitimate U.S.-based military weapons and hardware supplier, has been linked to a state-sponsored hacking group with links to Russia.
The new infrastructure was blamed on a threat activity group that Recorded Future tracks under the name TAG-53, but the cybersecurity community also calls it Blue Callisto, Callisto, COLDRIVER, SEABORGIUM, and TA446.
In a report released this week, Recorded Future’s Insikt Group stated, “Based on historical public reporting on overlapping TAG-53 campaigns, it is likely that this credential harvesting activity is enabled in part through phishing.”
The online protection firm said it found 38 areas, nine of which contained references to organizations like UMO Poland, Sangrail LTD, DTGruelle, Blue Sky Organization, the Commission for Global Equity and Responsibility (CIJA), and the Russian Service of Interior Issues.
The themed domains may be an adversary’s attempt to social engineer campaigns as genuine parties, according to speculation.
According to the findings of the researchers, “Notably, a consistent trend has emerged regarding the use of specifically tailored infrastructure by TAG-53 highlighting the long-term use of similar techniques for their strategic campaigns.”
The advancement comes almost four months after Microsoft uncovered that it did whatever it takes to disturb phishing and qualification burglary assaults mounted by the gathering fully intent on penetrating protection and knowledge counseling organizations as well as NGOs, think tanks, and advanced education elements in the U.K. what’s more, the U.S.
Venture security organization Proofpoint has additionally gotten down on the gathering for its complex pantomime strategies to convey rebel phishing joins.
In addition, the threat actor has been associated with a low level of certainty with a spear-phishing operation that targeted Ukraine’s Ministry of Defense at the same time Russia began its military invasion of the country in March.
In a separate article, SEKOIA.IO confirmed the findings, locating a total of 87 domains, two of which make reference to private companies Emcompass and BotGuard. Four non-governmental organizations (NGOs) working to alleviate the crisis in Ukraine were also targeted.
In an effort to evade detection from email gateways, the threat actor used a spoofed email address to send a spear-phishing message with a decoy PDF containing a fraudulent link, imitating a trusted source.
The cybersecurity company explained, “The email exchange shows that the attacker did not include the malicious payload in the first email, but waited to get an answer to build a relationship and avoid suspicion before sending the payload to the victim.”
Microsoft’s conclusion that SEABORGIUM targets Russian citizens living abroad, experts in Russian affairs, and former intelligence officials is strengthened by the use of typosquatted Russian ministry domains.
“War crime-related evidence and/or international justice procedures, likely to anticipate and build counter narrative on future accusations,” SEKOIA.IO said of the targeting of CIJA as an intelligence gathering mission.
Lupovis, a threat intelligence firm, recently disclosed that Russian threat actors are “rerouting through their networks” to launch attacks against Ukraine after compromising the IT environments of several businesses in the United Kingdom, the United States, France, Brazil, and South Africa.
Microsoft, on the other hand, has issued a warning about a “potential Russian attack in the digital domain over the course of this winter,” pointing to Moscow’s “multi-pronged hybrid technology approach” to carrying out cyber attacks on civilian infrastructure and influencing operations with the intention of igniting division in Europe.


 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years ago
 Vulnerabilities/Malwares3 years ago
Vulnerabilities/Malwares3 years ago
 Malwares3 years ago
Malwares3 years ago
 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years ago
 Windows/Mac/Linux4 years ago
Windows/Mac/Linux4 years ago
 Cyber Attacks/Data Breaches4 years ago
Cyber Attacks/Data Breaches4 years ago
 Mobile Hacking3 years ago
Mobile Hacking3 years ago
 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years ago