Malwares
Cybercriminals Use the Powerful BatCloak Engine to make malware undetected by AntiVirus
-

 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years agoSquarePhish: QR Code and Auth Device Code authentication Phishing tool
-

 Vulnerabilities/Malwares3 years ago
Vulnerabilities/Malwares3 years agoHyundai and Kia patch a bug that allowed USB cable car thefts.
-

 Ethical Hacking/Pen Testing4 years ago
Ethical Hacking/Pen Testing4 years agoHackBrowserData: Decrypt passwords/cookies/history/bookmarks from the browser
-

 Windows/Mac/Linux4 years ago
Windows/Mac/Linux4 years agoGoogle caught North Korean Hackers Using Chrome Browser Exploit on Americans
-

 Cyber Attacks/Data Breaches4 years ago
Cyber Attacks/Data Breaches4 years agoHackers from the Russian Federation have continued to launch attacks on Ukrainian organisations with info-stealer malware.
-

 Mobile Hacking3 years ago
Mobile Hacking3 years agoWhatsApp now supports proxy servers to bypass government restrictions.
-

 Ethical Hacking/Pen Testing3 years ago
Ethical Hacking/Pen Testing3 years agoRemotely exploiting Android devices using ADB (Android Debug Bridge) and Metasploit-Framework.
-

 Windows/Mac/Linux3 years ago
Windows/Mac/Linux3 years agoMicrosoft disclosed a recent Gatekeeper Bypass vulnerability in macOS.


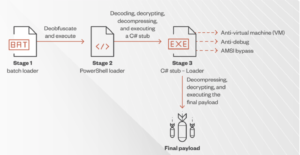 Since September 2022, various malware strains have been deployed using a fully undetectable (FUD) malware obfuscation engine known as BatCloak, consistently evading antivirus detection.
Since September 2022, various malware strains have been deployed using a fully undetectable (FUD) malware obfuscation engine known as BatCloak, consistently evading antivirus detection.