











[+] Warning This tool is developed for educational purposes. Here it demonstrates how ip-trackers work. If anybody wants to gain unauthorised access to someones IP-Address, he/she...


In order to address two zero-day vulnerabilities that were previously used by hackers to break into iPhones, iPads, or Macs, Apple has today published emergency security...


earlier this yr, North Korean hackers were the usage of a vital vulnerability inside the Chrome browser to target sufferers within the US, in line with...


A protection flaw in Apple Safari that become exploited within the wild earlier this year was at the start constant in 2013 and reintroduced in December...


A hazard actor running to in addition Iranian dreams is countryside to have been behind a hard and fast of disruptive cyberattacks towards Albanian government offerings...
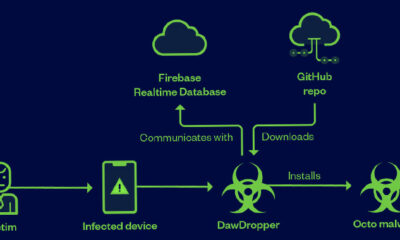
A malicious campaign leveraged seemingly risk free Android dropper apps on the Google Play save to compromise users’ gadgets with banking malware. These 17 dropper apps,...


An illicit on-line marketplace called SSNDOB was taken down in operation led by means of U.S. law enforcement companies, the department of Justice (DoJ) announced Tuesday.SSNDOB...


A risk actor is said to have “extraordinarily probable” exploited a safety flaw in an previous Atlassian Confluence server to set up a by no means-before-seen...


Twitter revealed on Friday that a now-fixed zero-day flaw was used to link phone numbers and emails to user accounts on the social media platform. “As...